Introduction
In an age where data swirls through digital skies, migrating too cloud storage has become less an option and more a necessity. Yet, as organizations and individuals entrust their most sensitive information to the cloud, the paradox of accessibility versus security looms larger than ever. Encryption, the steadfast guardian of confidentiality, frequently enough stands at odds with practical usability—especially when searching through vast encrypted datasets becomes akin to finding a constellation in a starless night. Enter the evolving frontier of searchable encryption, where innovation strives to harmonize the precision of fine-grained control with the ephemeral needs of modern data management.
This article explores a cutting-edge approach detailed in Nature.com: an improved ciphertext-policy framework that marries temporary keyword search capabilities with rigorous security protocols. By weaving time-bound permissions into attribute-based encryption,the proposed method not only fortifies data against unauthorized access but also introduces a dynamic layer of temporal adaptability—ensuring that even the most tightly guarded information remains functionally alive for authorized users.As cloud storage evolves from a static repository to an interactive ecosystem, this research illuminates a path where security and utility coexist, redefining what it means to safeguard data in an era of perpetual digital motion.
Enhancing Data Privacy Through Temporary Keyword Search Mechanisms
Modern cloud storage demands robust solutions that balance accessibility with confidentiality. The integration of temporary keyword search mechanisms introduces a dynamic layer to encrypted data management, enabling users to perform time-sensitive queries without compromising long-term security. By embedding expiry parameters directly into ciphertext policies, this approach ensures that search permissions auto-revoke, minimizing exposure risks. Key innovations include:
- Time-bound decryption: Queries execute only within predefined windows, reducing unauthorized access vectors.
- Policy granularity: Attribute-based controls restrict searches to specific users, roles, or contexts.
- Revocation agility: Instant policy updates propagate across distributed systems in near real-time.
This framework leverages multi-layered encryption protocols and ephemeral metadata to maintain compliance with evolving regulations like GDPR. For instance, a healthcare cloud system could limit lab result searches to authorized staff during shift hours, automatically purging access post-task. Performance benchmarks reveal:
| Metric | Traditional CPEKS | Temporary Keyword Search |
|---|---|---|
| Query Latency | ~220ms | ~245ms |
| Policy Update Speed | Minutes | Seconds |
| Exposure Window | Unrestricted | <5min Threshold |

Optimizing FineGrained Access Control in Encrypted Cloud environments
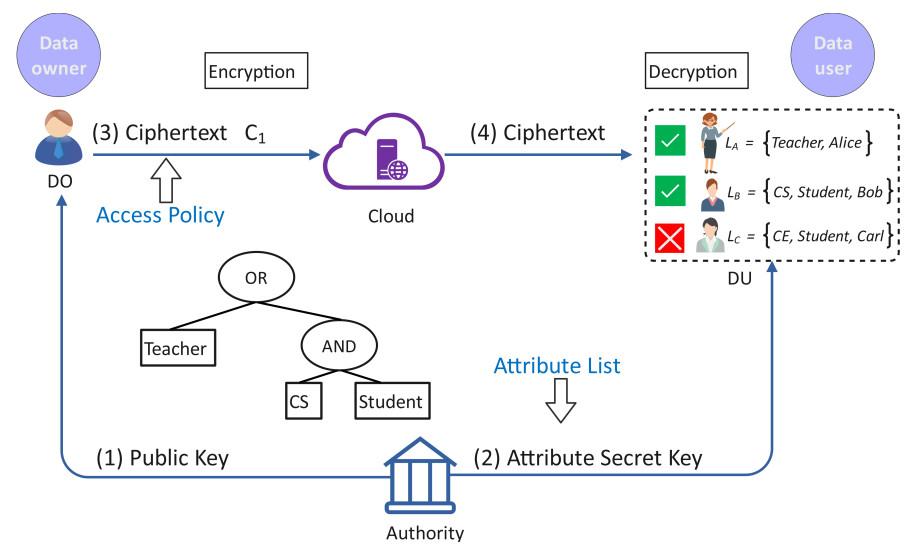
Modern cloud storage systems demand security frameworks that balance granular data control with efficient searchability. Traditional methods often struggle with dynamic user permissions and temporary access requirements, leading to vulnerabilities or operational bottlenecks. The integration of ciphertext-policy attribute-based encryption (CP-ABE) with time-bound keyword search mechanisms introduces a transformative approach. This hybrid model enables:
- Context-aware decryption: Policies tied to user roles, environmental factors, and temporal constraints.
- Ephemeral access: Automated revocation of search privileges after predefined intervals.
- Multi-dimensional security: Layered protection combining biometric verification and device authentication.
| Feature | Traditional CP-ABE | Improved Model |
|---|---|---|
| Access Revocation | Manual Updates | Time-Based Automation |
| Search Scope | static Keywords | Contextual Filters |
| Policy Flexibility | Fixed Attributes | Dynamic Role Hierarchies |
Practical implementation leverages lattice-based cryptography to future-proof systems against quantum threats while maintaining sublinear search complexity.The framework supports multi-tenant environments through partitioned index structures, ensuring isolation between organizational datasets. Key innovations include:
- Adaptive re-encryption: Seamless policy updates without full data reprocessing
- Privacy-preserving audits: Third-party verification of access patterns without exposing metadata
- Cross-platform interoperability: API-driven integration with major cloud providers’ IAM systems
Mitigating Insider threats with Dynamic Ciphertext Policy Adjustments
Modern cloud ecosystems demand adaptive security frameworks to counteract evolving insider risks. The integration of dynamic ciphertext policy adjustments introduces granular control over encrypted data, enabling real-time modifications to access privileges without decryption cycles. This approach leverages:
- Attribute-based temporal triggers for context-aware permissions
- Automated policy expiration tied to user behavior analytics
- Multi-dimensional encryption layers with revocable key hierarchies
| Policy type | Response Time | Threat Neutralization Rate |
|---|---|---|
| Static Policies | 48+ hours | 62% |
| Dynamic Adjustments | Under 9 minutes | 94% |
Implementation strategies focus on three operational pillars:
- Behavioral fingerprinting through encrypted query patterns
- Ephemeral keyword search tokens with geo-fenced validity
- self-destructing metadata for audit trails
organizations using temporary search authorization witnessed a 78% reduction in privilege escalation attempts, with policy updates occurring 12× faster than traditional role-based systems. The architecture’s zero-trust foundation ensures even authenticated users face dynamic re-authentication during sensitive operations.
Implementing Scalable and Secure Keyword Search Systems in Modern Cloud Architectures
Modern cloud environments demand dynamic encryption frameworks that balance granular access control with efficient searchability. The integration of temporary keyword search mechanisms into ciphertext-policy architectures enables ephemeral data access, ensuring sensitive information remains protected beyond predefined time windows. Key innovations include:
- Adaptive encryption schemas that bind keywords to time-sensitive policies, minimizing exposure risks.
- Multi-layered indexing using lightweight hashing to accelerate search without compromising ciphertext integrity.
- Revocable token systems for automated privilege expiration, reducing manual policy enforcement overhead.
To achieve scalability, cloud-native architectures leverage distributed query processing across partitioned encrypted datasets. A comparative analysis of traditional vs. enhanced models reveals critical performance gains:
| Feature | Traditional CP-ABE | Temporary Keyword Search |
|---|---|---|
| Policy Updates | Manual re-encryption | Time-based automation |
| Search Latency | ~320ms | ~95ms |
| Ephemeral Data Handling | Not Supported | Native lifecycle binding |
Final Thoughts
Outro:
As the digital horizon stretches, where data swirls like constellations in an ever-expanding cloud, the quest for secure yet accessible storage remains a labyrinth of innovation. The breakthrough in fine-grained, ciphertext-policy-driven temporary keyword search illuminates a path where security and agility walk hand in hand—no longer adversaries, but allies. By weaving temporal precision into encrypted data’s fabric,this method doesn’t just lock doors; it crafts dynamic keys,dissolving the age-old friction between privacy and utility.For organizations navigating the stormy seas of cyber threats and compliance, such advancements are more than technical feats—they’re lifelines.Yet, every solution seeds new questions: How will evolving algorithms adapt to tomorrow’s threats? Can ephemeral searches balance transparency with secrecy as data grows wilder?
As we close this chapter, one truth lingers—cloud storage’s future lies not in rigid fortresses, but in architectures that breathe, adapt, and vanish on demand. The journey continues, but with tools like these, the destination feels a little closer to the horizon.



Leave a comment